Fake Captcha Scam Spreads Lumma Stealer—How Are Hackers Fooling Victims?
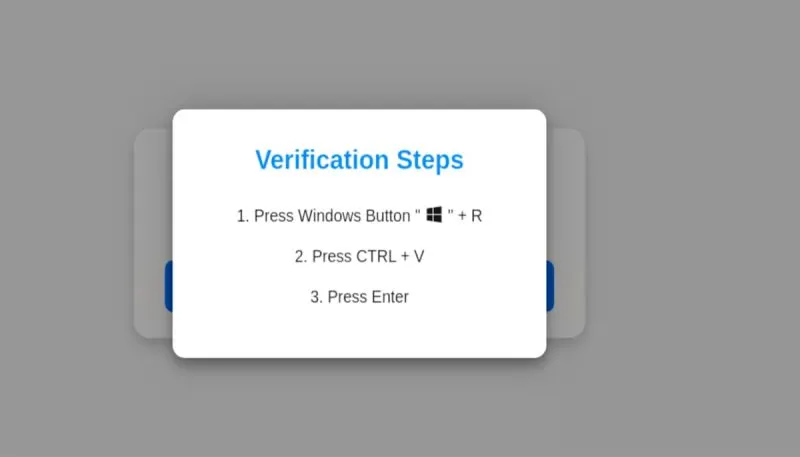
Cybercriminals are at it again, this time using fake CAPTCHA verification pages to trick users into spreading the Lumma information stealer. But how does a simple CAPTCHA turn into a full-blown malware infection?
image credits :hackread.com
The attack starts when a user lands on a compromised website and encounters a fake CAPTCHA page. Instead of a real verification check, the site instructs victims to copy and paste a command into Windows’ Run prompt. This command downloads and executes a malicious script, launching Lumma Stealer while bypassing browser security defenses.
Lumma Stealer, a malware-as-a-service (MaaS) tool, has been increasingly active, targeting industries like healthcare, banking, and telecom. Hackers constantly tweak delivery methods to evade detection, making it harder for security tools to keep up. And it’s not just fake CAPTCHAs—1,000+ counterfeit domains impersonating Reddit and WeTransfer have been spreading Lumma through deceptive downloads.
Worse still, phishing attacks are evolving. A new toolkit, Tycoon 2FA, is designed to bypass security checks and evade detection by automated scripts. Attackers even use Gravatar profiles to mimic major services like AT&T and Proton Mail, luring users into credential theft.
With threats growing more sophisticated, one question remains: Are businesses and individuals equipped to recognize and stop these scams before they strike?


















Comments