Hackers Hijack Wordpress Sites To Spread Malware—Are You At Risk?

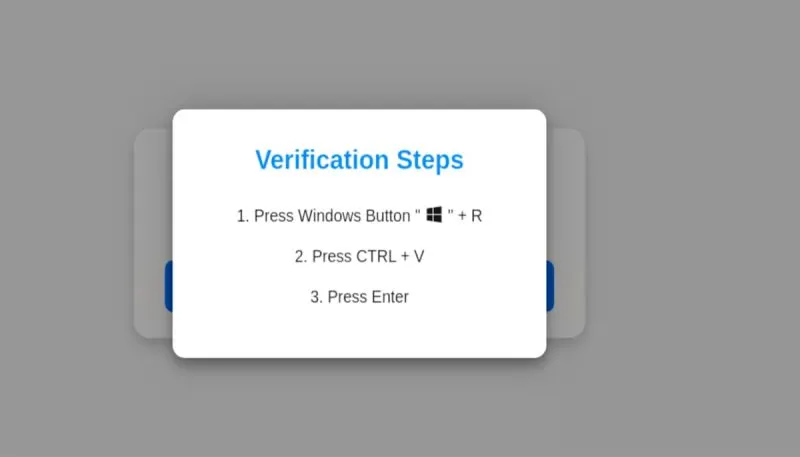
Hackers are exploiting outdated WordPress sites to push password-stealing malware onto unsuspecting users. Thousands of compromised websites now display fake Chrome update prompts, tricking visitors into downloading malware designed to steal sensitive data.
Security firm c/side uncovered the attack, which remains active. Some of the hacked sites rank among the most visited on the web. The malware, Amos for Mac and SocGholish for Windows, steals login credentials, cookies, and crypto wallets, fueling further cyberattacks.
Researchers describe this as a "spray and pray" attack—indiscriminately targeting anyone who lands on these sites. Despite its simplicity, the method has proven effective, as many users fall for the fake update prompt and manually install the malware.
C/side has identified over 10,000 affected sites and alerted Automattic, WordPress's parent company. However, WordPress maintains that third-party plugin security is the responsibility of developers. This hands-off approach leaves many site owners vulnerable.
Security experts warn that even Apple's built-in protections require user caution. Once installed, these malware strains can grant hackers access to critical accounts. The lesson? Never download browser updates outside official channels.
With credential theft behind some of the biggest cyberattacks in history, the question remains—how many more users will fall victim before these tactics are stopped?

















Comments